VA+ (Vulnerability Assessment Plus) Supporting Notes.
Below are details about the exam which will help you with self-study. This is not a formal or comprehensive guide, it is a supplement to any self-study or course you might choose.
Please contact us if you have any queries.
Networking
There are a significant number of networking questions in the multiple-choice examination and you are expected to be able to configure and troubleshoot networking from both the terminal and from a GUI. You are expected to be familiar with the following terms and concepts.
Addressing
- IP addresses, classes of networks, subnet masks, broadcast addresses default gateway, DNS server, CIDR notation, RFC 1918 private addresses, Network Address Translation (NAT) techniques.
- Decimal Dotted Octets, e.g., 192.168.14.1 & binary equivalent 11000000.10101000.00001110.00000001 and how to convert between decimal, binary (& hexadecimal where appropriate).
- You should be able to identify a valid routable IP address from either an invalid address or one that is not intended to be routed across the Internet. So 259.121.1.1 being invalid and 172.16.2.1 being part of RFC 1918 and should be classed as non-routable (you can obviously do as you choose internally).
- You should know what MAC addresses are, what layer MAC is in the OSI and TCP models (Data Link in the OSI and Network Access layer in the TCP\IP model) and how they are organised and represented.
- [OUI|ID] For example, in the MAC address 98-8b-5d-93-c9-23, which part is the OUI (Organisational Unique Identifier)? What does the MAC broadcast address look like? The first 24 bits or 6 hex digits (shown in bold above) represent the OUI and FF-FF-FF-FF-FF-FF is the broadcast MAC address.
An excellent networking primer can be found here. It takes the form of a TCP\IP Tutorial and Technical Overview, and covers IP addressing and almost every other protocol you will need to know about.
If you are unsure about number conversions, have a look here or at this simple example here. This covers decimal to binary and vice versa.
Network Configuration
- You should be able to use basic networking tools to configure and test an IP address and a route to a host. Examples of tools include ip a, ip r, ifconfig, route, ping, traceroute, arp.
Network Devices, Routing & Media
- Switches provide connectivity for LANs and provide micro segmentation. Switches are layer 2 devices (data link in OSI, Network Access in TCP\IP) and their Protocol Data Units (PDUs) are ‘frames’. Switches work with MAC addresses and can only determine addresses locally. If a frame is leaving a LAN, it will invariably do so via the default gateway.
- Routers are responsible for determining the path to and end system. Routers operate at layer 3 (network layer in the OSI and in TCP\IP). Routers work with packets (or datagrams) as their PDU. Routers tend to use dynamic routing protocols, such as RIP, EIGRP, OSPF, IS-IS BGP, EGP, etc to maintain routing information about the networks they are attached to. It is possible to configure static routing, however most routers will be using some form of dynamic routing protocol as previously discussed.
- Some routing protocols are known as Distance Vector (DV) routing protocols , whilst others are known as Link State (LS) routing protocols. A DV routing protocol tends to use less metrics than a LS and a router will normally only know about routes offered by its directly connected neighbours, whilst a LS will hold information about all of the routes within an administrative domain and has more complex metrics. Obviously there can be finer grained choices made when you have more metrics, so a LS routing protocol will generally perform significantly better than a DV routing protocol, however, there are instances where a DV may perform just as well or at least not so poorly as to be ignored as a choice.
- It is an advantage to know the difference between and Interior Gateway Protocol (IGP) and an Exterior Gateway Protocol (EGP). IGPs tend to be used within the administrative control of a network, whilst EGPs tend to be used when systems under different autonomous control are being connected.
- WLAN access points provide connectivity to wireless networks for hosts and in terms of their operation act more like hubs than switches. An access point will use the CSMA\CA (Carrier Sense Multiple Access with Collision Avoidance) protocol for media access and likely some form of WPA for security.
- You should have a basic understanding of types of media such as wire, fibre, wireless etc. Each media has its advantages and disadvantages.
- Wire tends to be Ethernet (UTP or STP, Unshielded Twisted Pair and Shielded Twisted Pair respectively) and the current specifications range from 1Gb to approx 40Gb. There are many in-between and beyond. However, installations will often specify the network as a cable type, for example Cat 6e, which is actually a cable specification. Wire has the advantage that it can bend relatively easily and in terms of connection points is relatively easy to work with. It does have distance limitations, so is limited to runs of 100m after which the signal must be amplified in some way. However, wire does suffer from noise and can be significantly diminished by EMI (Electromagnetic Interference), consideration must be taken during installation.
- Fibre has some significant advantages as it does not suffer from EMI and can have extended runs many times that of wire and significantly increased bandwidth. In fact some under sea cables have runs of up to 240km. However, making connections and splicing fibre is much more difficult. Fibre optics also have only a limited capacity for bending, so are more difficult to install where significant cable bending is required. Fibre optic is also significantly more expensive than its wired counterparts are. However, costs continue to fall and fibre is often used for site-to-site links and for horizontal backbone cabling
- Wireless transmissions have the advantage of not requiring a ‘physical’ connection to the network, however this does mean that the signals are ‘seen’ by all as they travel through the air. It is of course possible to use encryption and WPA & WPA2 offer some form of protection, however there does need to be a judicious approach to the selection of passphrase and frequency of change. WLANs can be affected by physical obstructions and atmospheric conditions. They tend to offer lower bandwidth and the bandwidth diminishes as the number of users attached to an access point increases, however they provide flexibility.
OSI Reference Model & TCP\IP Suite Concepts
- The OSI (Open Systems Interconnection) Model is a reference model created by the ISO (International Standards Organisation).
- The main aim was to ensure that networks were interoperable and remove ‘vendor’ issues from the ability of one network to communicate with another. The OSI model has seven layers.
- Working from top to bottom: Application, Presentation, Session, Transport, Network, Data Link & Physical. Each layer has a well defined purpose and operates on data known as Protocol Data Units (PDUs).
- Data is encapsulated and de-encapsulated in these PDUs when moving both down and up the layers.
- The process of encapsulation is shown below. The top three layers deal with data, whilst the bottom four layers deal with their respective PDUs, namely segments, packets, frames and bits.
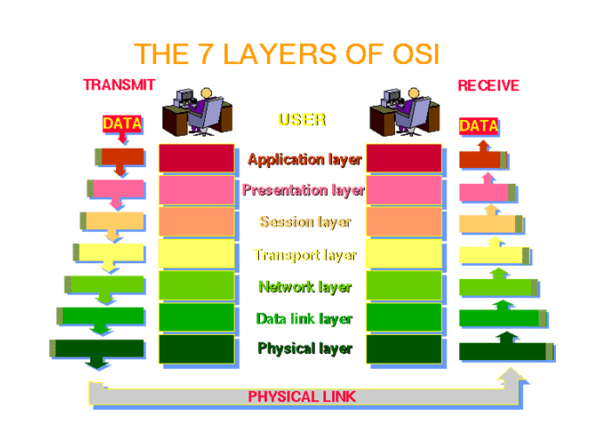
The TCP/IP model has only four layers. The layers map to the OSI as follows:
OSI
7. Application
6. Presentation
5. Session
4. Transport
3. Network
2. Data Link
1. Physical
TCP\IP & some protocols at each layer
7.
6. Application [FTP, Telnet, SMTP, POP, DNS, RIP…]
5.
4. Transport [TCP, UDP, ICMP, IGMP]
3. Internet [IP, IPSEC]
2.
1.Network Interface [Ethernet, Token Ring, Frame Relay…
OSI Model Layer Functions
The OSI model’s seven layers map as previously shown to the TCP\IP model’s four layer approach. In some cases a TCP\IP layer straddles a number of layers of the OSI model.
7. Application Layer
The application layer provides network services (processes) to applications. For example, a computer on a LAN can save files to a server using a network redirector supplied by a Network Operating System. Network redirectors allow applications like Word and Excel to “see” the network. Typical protocols here include FTP, HTTP, HTTPS, DNS, SSH, POP etc.
6. Presentation Layer
The presentation layer provides data representation and code formatting. Code formatting includes compression and encryption. Basically, the presentation layer is responsible for representing data so that the source and destination can communicate at the application layer. Examples, JPEG, MPEG, ASCII, EBCDIC, HTML.
5. Session Layer
The session layer provides inter-host communication by establishing, maintaining, and terminating sessions.
Session layer uses dialog control and dialog separation to manage the session. Some session protocols include: NFS (Network File System), SQL (Structured Query Language), RCP (Remote Call Procedure), ASP (AppleTalk Session Protocol), SCP (Session Control Protocol) and X-window.
4. Transport Layer
The transport layer provides reliability, flow control, and error correction through the use of TCP (Transmission Control Protocol). TCP segments the data, adding a header with control information for sequencing and acknowledging packets received. The segment header also includes source and destination ports for upper-layer applications TCP is connection-oriented and uses windowing. UDP (User Datagram Protocol) is connectionless. UDP does not acknowledge the receipt of packets and has a lower overhead than TCP.
3. Network Layer
The network layer is responsible for logically addressing the packet and path determination. Addressing is achieved via routed protocols such as IP, IPX, AppleTalk, and DECnet. Path selection is achieved via routing protocols such as RIP, IGRP, EIGRP, OSPF, and BGP. Routers operate at the Network Layer and make best path determinations based on IP addresses.
2. Data Link Layer
The data link layer provides access to the media in use. It handles error notification, network topology issues, and physically addressing the frames. Media Access Control will be through either a deterministic method, such as token passing or non-deterministic, such as a broadcast topology (there will be collision domains). Two important concepts here are: CSMA/CD, which is used in Ethernet networks and CSMA/CA used in WLANs.
1. Physical Layer
The physical layer provides electrical, mechanical, procedural and functional means for activating and maintaining links between systems. This Includes the medium through which bits flow. Media can be CAT 5/5e/6/6a/6e/7… cable, coaxial cable, fibre optic cable, the atmosphere (WiFi) microwave, or infra-red light.
Linux Skills
It is quite common when undertaking commercial training in this space that you will be expected to be able to use Linux to:
1. Navigate and manipulate files and directories in a standard Linux file-system. The following commands would be essential: pwd, cd, ls, cp, mv, cat, echo, more, less, touch
2. Manipulate file permissions using chmod
3. Identify running processes using ps and use kill to end processes
4. Run processes in the background using &
5. Use the standard input and output redirection operators < > to redirect from and to files
6. Get help using man pages (or #command –h, where appropriate)
7. Use basic networking commands, ip a, ip r, ifconfig, route, ip, dhclient, arp, ping, traceroute etc.
8. Configure networking from the command prompt where appropriate (ifconfig, route, iproute2 tools)
9. Configure networking from the GUI (set IP address, subnet mask, default gateway and DNS Server)
10. Use some form of text editor (anything, vi, emacs…)
Linux File-system
In addition to the above, it is essential that you have some understanding of the Linux file-system, the location of files and the fact that Linux treats everything as a file. The following shows where files live in most distribution of Linux, many of the directories are the same regardless of the Linux distribution. There may be some variance in this depending on your specific distribution. A ‘typical’ directory structure shown below.
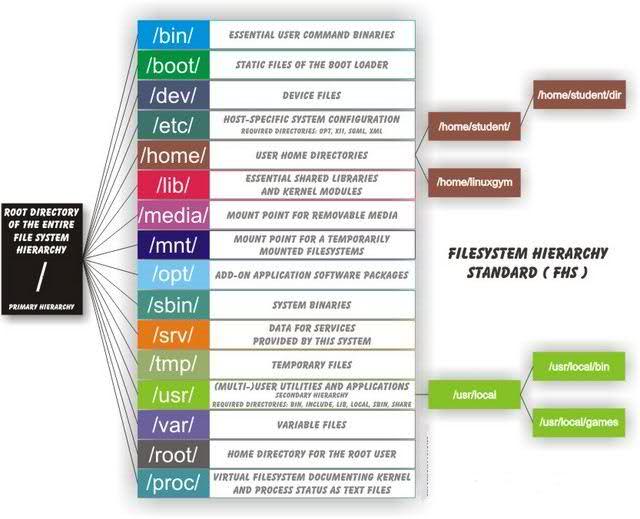
Filenames
Filenames in Linux can be up to 255 characters, however filenames cannot contain a forward slash (/) or the NUL character. The name may contain spaces, newlines, unprintable control characters, and characters from non-English languages. This means that it is possible to have a file or directory name that is entirely made of blanks or backspace characters. Not that this will be particularly usable, however it is possible (and may be used when someone is trying to hide something they do not want you to see, or is part of a rootkit which is obfuscating its own files). An extremely useful resource related to filenames, paths and navigation is available here.
Paths
It is essential to understand the notion of absolute and relative paths. The following are examples of each and should really be second nature to anyone using Linux regularly.
/ <- This will be an absolute path.
. <- From where you are current directory
../ <- From the parent directory (so can be put together ../../../ for as many as required)
~ <- From a $HOME directory (if logged in as root, this will be /)
Absolute & Relative Paths
1. Any path supplied from the root directory / is known as absolute path.
2. So the path to ip_forward is: /proc/sys/net/ipv4/ip_forward is an absolute path the file ip_forward.
3. Let’s assume you are already be in the /proc directory, the relative path would the be sys/net/ipv4/
4. It is possible to specify paths using the ../../ (basically means “up to parent/up to parent”) path to a folder, so if you were in say /etc/shadow and wanted (for some reason) to specify a path without starting from root, you could specify ../../proc/sys/net/ipv4/, which again would provide a path to the ip_forward file.
5. Additionally, if you are logged in as a specific user, you have a $HOME directory, which can be specified using the tilde ~, so if your home directory was /home/student/harry and you wanted to change to this from anywhere, you can simply type $ cd ~ and you will be transported to your home directory.
6. This also means that you can specify paths to your home directory structure such as $ cd ~/pentest, which would be equivalent to $ cd /home/student/harry/pentest
7. The . can be very useful as it indicates that you wish to do something with respect to the present working directory (pwd). For example $ cp /proc/sys/net/ipv4/ip_forward . This would copy the file ip_forward to the present (or current) working directory.
8. There are many reasons for using the various different ways to specify paths and commands. For example, a command such as $ ./configure is a good example of specifying exactly which command you wish to execute. Had there been a file in your ‘global’ path called configure, it would likely take precedence over a local file called configure hence the ./ to ensure that the file in the current working directory is executed.
Legal Issues
There are a number of UK laws that a penetration tester must be aware of and have a basic understanding of.
The Computer Misuse Act (1990) and some content of The Police and Justice Act (2006)
- Section 1. Unauthorised access to computer material, punishable by 6 months’ imprisonment or a fine “not exceeding level 5 on the standard scale” (currently £5000);
- Section 2. Unauthorised access with intent to commit or facilitate commission of further offences, punishable by 6 months/maximum fine on summary conviction or 5 years/fine on indictment;
- Section 3. Unauthorised modification of computer material, subject to the same sentences as section 2 offences.
- The PJA (2006) proposes some changes to the CMA (1990), which are not yet in effect. Sections 35— 37 relate to reckless activities & the making & supply of tools or equipment intended for hacking.
Research Task
Researching the following would be useful to you: DNS, DHCP, TCP, UDP and SNMP. For example, what do the acronyms stand for.





